a ) Security Assessment and Risk Assessment
The objective of the ICT Security and Risk assessment is to provide an overall view on an annual basis of the institution’s security and risk posture across a range of IT domains and identify areas for improvement. Each review includes a report that documents the observations noted along with recommendations.
Security best practices recommend frequent Security and Perimeter Assessments to identify potential vulnerabilities that may be exploited.
An overall security and perimeter scan, the application level assessments. Clients can choose from the following options;

Services
- Infrastructure
- Web Applications
- Cloud Infrastructure
- Cloud Application
- Penetration test
b ) ICT Policy Reviews and Development
ICT Security Policies play a critical and strategic role in ensuring an institution’s information is managed appropriately and securely. It is important that policies are reviewed and updated on a regular basis to ensure they are in line with business requirements and industry best practices.
Our Security team delivers an in-depth analysis of a selection of the institutions current policies along with assisting on the creation new policies.
ICT Audit Services
Our team has been offering ICT Audit services to different companies for years to help them understand and implement solutions relating to a rapidly changing technology environment. Using that same sense of teamwork and partnership, we offer Information Technology (IT) audit services focused on helping clients reduce risk while increasing efficiency and effectiveness.
We evaluate IT general controls and system applications, and integrate information technology throughout the audit process. Our unique approach seeks to automate and improve internal controls.
We evaluate IT general controls and system applications, and integrate information technology throughout the audit process. Our unique approach seeks to automate and improve internal controls.
IT Audit Services Performed
Services
- IT audit outsourcing and co-sourcing, covering all IT operational and business risk
- Penetration testing and assessments
- Internal and external network scans
- Social Engineering
- Risk Assessments
- Privacy Impact Assessments (PIA)
- SSAE SOC Reports
- PCI Readiness Assessments
- Security Assessments, including disaster recovery and business continuity
- Integrated IT, financial, operational and compliance audits
- External auditor relationship management
- IT process reviews (access, SDLC, change management, operations)
- SOX 404 documentation and controls testing
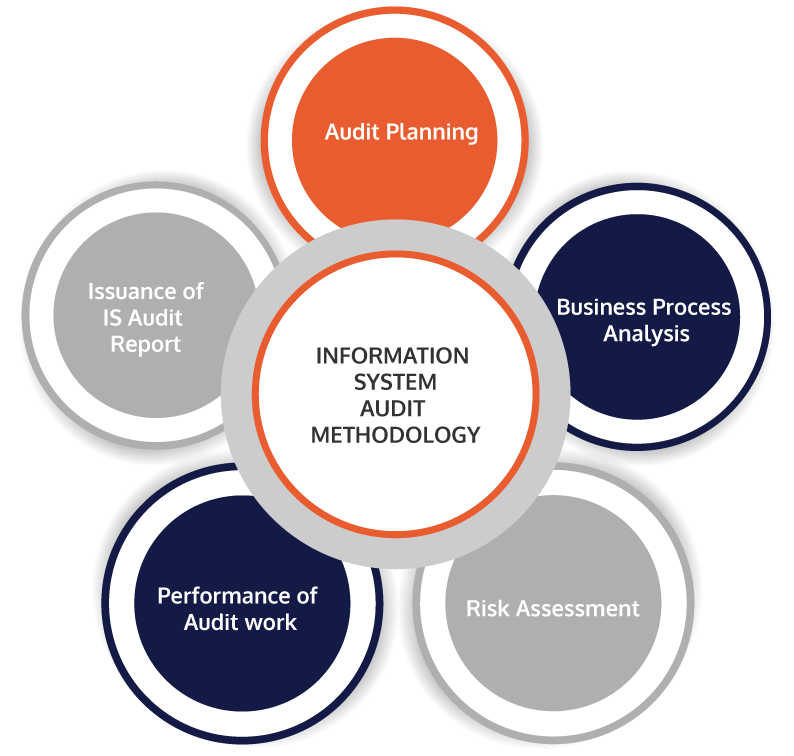
Our Audit Methodology is summarized as below;
c ) Forensic Investigation
OneSpan provides deep, expert analysis of intrusion incidents and examination of your current organizational and technical environments, to determine the root cause of the breach, identify who or what is responsible, and provide recommendations for improvement.

Our forensic investigations generally include:
- Gathering information about the incident from servers, workstations, transferable media, and network equipment
- Collecting data from service providers (via law enforcement requests)
- Creating an expert, reliable, and factual account of the incident on the basis of the information collected
- Forming conclusions about the cause of the incident and (when possible) the persons responsible
- Recommending preventative measures to avoid future incidents
c ) ICT Governance
IT governance emphasizes Information Technology Systems, their risk management, and its performance. It ensures that the investments made on IT yield fruitful results, which mitigate IT-associated risks and threats.
At OneSpan we help an organization to align IT governance with the business strategy to achieve maximum efficiency out of Information Technology Systems by implementing strategic goals. IT governance helps in balancing the risks and the adoption of the industry’s best practices in order to have more control over ensuring regulatory compliance.
c ) Business Process Improvement
As OneSpan we work closely with organizations to improve the functionality and efficiency of their business processes and workflows. We accomplish this through a suite of services that complement the most current and proven business process reengineering best practices. We help improve desired processes within your organization through:
- Business Analysis: Through business analysis we help organization in identifying their business needs and determining solutions to business problems. Solutions often include a software-systems development component, but may also consist of process improvements, organizational change or strategic planning and policy development.
- RFP and RFQ Development: Requests for Proposal and Requests for Quotation are documents that request specific solutions to a problem, as well as pricing options for those solutions. Development of these requests is essential to identifying the best source of a service. Through concentrated analysis, we businesses develop the best RFPs and RFQs for their needs.
- Workflow Analysis: Workflow Analysis services look at your existing business processes to identify bottlenecks and repetitive activities and implement more effective solutions. The goal of this process is to streamline workflows for maximum efficiency.
- Systems Analysis and Recommendations: Too many companies make use of outdated or inefficient systems. To help you determine the status of your system(s) and make upgrades, we will identify the needs of your business, assess how well your system stacks up and make recommendations for improvement.




